Sistem menadžmenta bezbednošću informacija (ISMS) ISO/IEC 27001
ISO/IEC 27001 – Information Security Management Systems Implementation and Certification
ISO/IEC 27001 Information Security Management Systems standard ensures that your organization keeps information assets safe and secure, by building an information security infrastructure against the risks of loss, damage or any other threat. Companies that obtain ISO/IEC 27001 implementation and certification validate that the security of financial information, intellectual property, employee details, assets or information entrusted from third parties is being successfully managed and continually improved according to best practice approaches and frameworks.
IMPLEMENTACIJA PROJEKTA USAGLAŠAVANJA SA ZAHTEVIMA ISO/IEC 27001 U VAŠOJ ORGANIZACIJI!!
Pozovite, pošaljite e-mail, zatražite PONUDU po meri Vaše organizacije, ODGOVOR očekujte istog dana!
We help organizations to show commitment and competence with internationally recognized standards by providing this assurance through the education, implementation, evaluation and certification against rigorous, internationally recognized competence requirements.
IST experts are here to assist you throughout the entire process and if you need help getting started follow the link below and contact us to begin with the first step.
If you need help getting started in IST with PECB training for Certified ISO/IEC 27001 Lead Implementer and Lead Auditor, contact us to begin with the first step.
Benefits of ISO/IEC 27001 implementation and certification to your organization:
- Provides physical and environmental security across all management processes
- Provides you with a competitive advantage
- Reduces costs due to incident and threat minimization
- Demonstrates compliance with customer, regulatory (EU GDPR if needed) and/or other requirements
- Sets out areas of responsibility across the organization
- Communicates a positive message to staff, customers, suppliers and stakeholders
- Integration between business operations and information security
- Alignment of information security with the organization’s objectives
- Puts forward true value through enhancement of marketing opportunities
Benefits of ISO/IEC 27001 implementation and certification to your customers:
- Keeps customers intellectual property and valuable information secure
- Provides customers and stakeholders with confidence in how you manage risk
- Secures exchange of information
- Ensures customers that you are meeting your legal obligations
- Enhances satisfaction of the delivery of your service or products
ISO 27k FAMILIY OF ISO STANDARDS
During the Project of ISO 27001 implementation it is extremely important to use other guidelines and guidances from ISO 27k Information Security family of ISO standards. For that purposes it is necessary the usage of ISO/IEC 27002 and ISO/IEC 27005 standards.
CYBER SECURITY AND APPLICATION SECURITY ARE IMPORTANT ISSUES FOR THE ESTABLISHMENT OF THE COMPREHENSIVE ISMS FRAMEWORK BASED ON ISO 27001
The ISO/IEC 27032 standard is essential for all businesses to utilize. The risk of security threats is increasing on a daily basis as we rely more on the cyberspace. However, the ISO/IEC 27032 standard provides guidelines regarding the protection and long-term sustainability of business processes. In addition, it equips individuals with the ability to develop a policy framework on which identifies the processes that are the most vulnerable to cyber-attacks; and that must be considered in order to ensure that business and clients will not be at risk.
The ISO/IEC 27034 provides a systematic approach that guides organizations to implement security concepts, principles, and processes in the application security structure. Application security is an international concept that supports the information security framework and guides an organization towards achieving a solid information security structure within its operations.
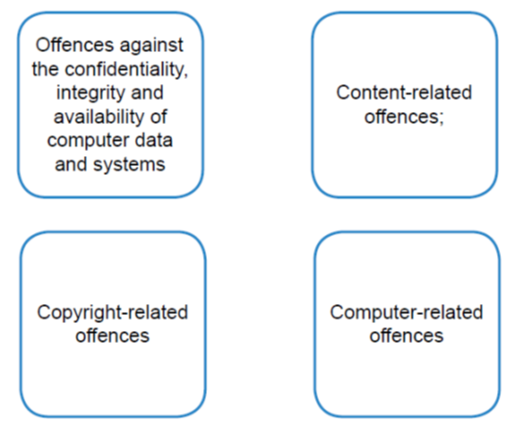
The term cybersecurity we can find in ISO/IEC 27032 and can be regarded as the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that can be used to protect the cyberenvironment and organization and users’ assets (definition according to the International Telecommunication Union (ITU) Recommendation X.1205).
If information security is breached, the repercussions can range from heavy penalties to legal action and reputational damage that could threaten the viability of the business or have a major impact on the funds available to deliver services.
ISO 27799 Information Security Management in the Healthcare Industry
This standard provides guidelines to support the implementation of information security controls in healthcare organizations based on ISO/IEC 27002.
By following the guidelines of this international standard, healthcare organizations will be able to maintain a level of security that is suitable to their conditions and will help to ensure the availability, integrity and confidentiality of their personal health information. Basically, ISO 27799 serves as a tool to protect personal health information.
IST Aproach to the Information Security Management Systems implementation
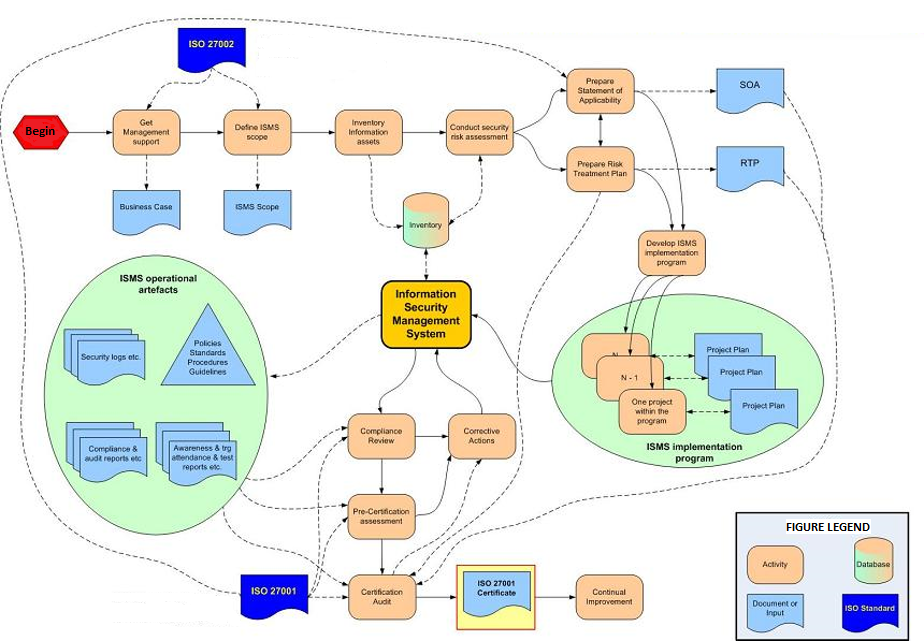
The Deming cycle follows the process approach, which allows the ISMS management systems implementation process to use the requirements and the expectations of the stakeholders as inputs, understand how it produces these requirements with the necessary actions and processes, and also verification of the management system results.
The figure shows how each clause of the ISMS management systems can potentially be implemented by following this structure. This structure includes mainly the requirements that are generic and existent in almost all the management systems. However, it should be adjusted based on the ISO/IEC 27001 standard that the organization is implementing and include additional clauses as necessary.
IST experts are here to assist you throughout the entire process and if you need help getting started follow the link below and contact us to begin with the first step.
If you need help getting started in IST with PECB training for Certified ISO/IEC 27001 Lead Implementer and Lead Auditor, contact us to begin with the first step.
IST as Authorized PECB Gold Partner offers the ISO/IEC 27001 Information Security Management training and certification that helps your organization secure their valuable information. Prove that you have the knowledge and competence on creating a safe Information Security Management System, a system which reduces the threats towards your intellectual property, and most importantly, is customized for your organization.
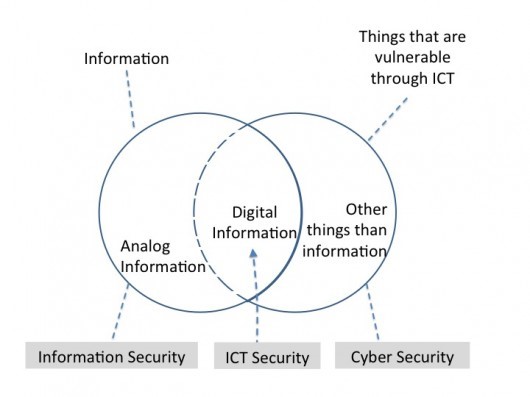
Bezbednost informacija postaje sve važnija u modernom društvu. Savremeni državni i privredni subjekti sve više zavise od Informaciono-komunikacione (IKT) infrastrukture. To omogućava protok velike količine informacija između subjekata, ali ujedno izlaže informacije i informacione sisteme brojnim pretnjama. Pojam bezbednosti informacija ne odnosi se isključivo na tehničke mere zaštite (lozinke, kriptovanje, prava pristupa, mrežnu bezbednost i sl.), već ISO 27001 podrazumeva i administrativne (sigurnosne politike, pravilnike, procedure usklađene sa zakonima), fizičke (video nadzor, zaštita prostorija, fizička kontrola pristupa itd.) ali i organizacione mere (podela dužnostii odgovornosti za bezbednost, rad sa ljudskim resursima i dr.).
Kada govorimo o standardu ISO 27001 prvenstveno mislimo na informacije, jer one predstavljaju suštinu poslovanja najvećeg broja kompanija u današnje vreme i može biti kreirana i korišćena u različitim oblicima: napisana na papiru, u elektronskom obliku, poslata klasičnom poštom ili elektronskim sredstvima, pomenuta u razgovoru i sl. U veoma oštroj konkurentskoj borbi, zaštita informacija je neophodna jer postoje pretnje po informacionu imovinu iz raznih izvora. Ti izvori pretnji mogu biti interni, eksterni ili slučajni, a sve češće pretnje nastaju usled zloupotrebe novih moćnih tehnologija. Vaša sposobnost da uspešno poslujete zavisi od sposobnosti vaše organizacije da efektivno i efikasno upravlja rizicima (verovatnoća da će neka pretnja iskoristiti postojeće ranjivosti informacionih sredstava i napraviti štetu) što upravo nudi internacionalni standard ISO 27001.
Pogledajte kako bi izgledale moguće faze implementacije standarda ISO 27001 u vašoj organizaciji:
I faza
- upoznavanje zaposlenih sa projektom, formiranje projektnog tima
- snimak stanja postojećih sistema menadžmenta (npr. QMS, EMS..) i ISMS sistema
- gap analiza – intervjui, anketiranje rukovodstva i ključnih zaposlenih
- izveštaj o usaglašenosti postojećih sistema (QMS, EMS, OHSAS..) i ISMS sa zahtevima standarda
II faza
Edukacija zaposlenih – rukovodstva i radnog tima za uvođenje i primenu standarda ISO 27001. posebna personalna sertifikacija jednog ili više zaposlenih (ISMS menadžera obavezno) za internog auditora prema programu američke kuće Exemplar global (rab qsa+inarte)!
III faza
- utvrđivanje konteksta ISMS organizacije
- određivanje opsega ISMS
- ažuriranje politika postojećih sistema menadžmenta i definisanje politike bezbednosti informacija (ISMS)
- planiranje ISMS
- procena rizika, izrada asset registra informacione imovine, analiza rizika i tretman rizika, uticaj na poslovanje
- definisanje kontrolnih ciljeva i sigurnosnih kontrola (SOA)
IV faza
- ažuriranje dokumentacije postojećih standarda (QMS npr…ako postoje)
- ažuriranje qms poslovnika (uslovno)
- projektovanje, razvoj i izrada dokumentacije ISMS
- verifikacija dokumentacije ISMS
- integracija ISMS i postojećeg sistema menadžmenta (qms, ems, ohsas..)
- implementacija dokumentacije ISMS u radne procese
- organizovanje i sprovođenje interne provere ISMS
- analiza neusaglašenosti i sprovođenje korektivnih mera ISMS
V faza
- pripreme za sprovođenje eksterne predsertifikacione provere ISMS
- preporuke za stalno poboljšavanje ISMS sertifikovanog prema ISO 27001






